This is xTX-SHIELD Private Payments: Full Privacy, Regulatory, High Performance Payment Agreements driven by First Native Stabilization Currency
THE PRIVACY ENFORCEMENT CAPACITY OF THE SUB-CHAIN IS BASED ON TX-SHIELD ' S SUB-CIPHERIC STRUCTURE, WHICH INTEGRATES ITSELF AT THE CHAIN LEVEL AND TOGETHER CONSTITUTES THE INFRASTRUCTURE FOR STABLE CURRENCY PRIVACY SETTLEMENT。


This post is co-authored by x TX-SHIELD:

Privacy payments must be a chain-level primary infrastructure
In the current block chain ecologyPrivacyIt's often seen as oneOptional External Functions, exists in the form of an independent DApp or a two-tier agreement (Layer 2). While flexible, this “plug-in” model leads to performance bottlenecks, vague compliance and fragmentation of user experiences。
Sub-chainThe core proposition and product positioning is the complete inclusion of privacy paymentsThe original capacity of the chain layer, directly internal to the bottom of the public chain. This means that privacy is no longer an “option” requiring additional installation at multiple costsAnd it's all the top applications --EspeciallyStable currency ecology - basic services and platform capacity readily available。
The privacy payment function of this score will be related to its ecological applicationBen Pay Depth docking and withStabilized currency payments Gas, sponsorship transactions, first-key issuance RWAThe function on the chain forms a connection. BenPay will provide full access to privacy capabilities in the areas of payment, transaction and account systems, provide interface support for cross-border settlements, daily consumption and payment scenarios, and promote the inclusive and scale-down of privacy payments。
In the meantimeSub-chainThrough core infrastructure buildersTX-SHIELD CooperationI don't knowBased onMULTIPLE SECURITY CALCULATIONS (MPC)The privacy program is embedded in the chain layer. This is..Enterprise levelUsers offer oneHigh performance, compliance and privacyBothNew currency settlement。
TX-SHIELD is a technology company for the development of privacy payment algorithms. It is a public chain to stabilize currency distributors and DEX to develop a one-stop solution that is regulatoryly friendly and protects privacy. & nbsp; www.tx-shield.com
Why must it have to be a chain of primitives? The Iron Triangle for Performance, Security and Compliance
Embedding privacy logic in the chain is not just a technical realization option, but a deep response to performance, safety, compliance and commercialization needs。
Integration of performance and cost: elimination of “plug-in” costs
Traditional externalities, such as second-tier protocols or comminglers, often require users to cross the asset chain, generate zero-knowledge proof or signMultiple payment of fees, and bear the extraDelayI don't know。
- Compute privacy logic and trade settlement mechanismsInline Unified, achievableGas Integration of CostsI don't know. Realization of “one settlement, full privacy” and avoidance of multiple transaction costs and delays caused by the fragmentation of the cost of proof/signatures into processes across or below chains。
- It's a primary integration that makes sure it works at the enterprise levelEfficiencyandLow costThe rigid demand。
Enhanced security and “controllable privacy”
The ability of the chain layer allows us to..Nodal governance, remote certification and audit interfaceDepth integration. This not only strengthens the trust base based on decentrization, but also delivers the key “controllable privacy” architecture:
- Privacy enforcement is both centralized and capable ofCompliance when requiredProvide “optional disclosure” controlled channels。
- Users and agencies can present them to compliance bodies through selective disclosure mechanisms, as necessaryAudit certificates or regulatory information, implementing privacy protection and regulatory requirementsBalanceI don't know。
3. Compliance friendly
As the demand for compliance and control by financial institutions continues to rise around the world, the demand for financial institutions to comply with the rules of law and order has increasedCompliance costsIt has become one of the keys to limiting Web3 scale applications。
- The chain layer is designed to allow us to..Compliance interface(selective disclosure, regulatory views, audit certificates) and privacy functionsSync DesignI don't know。
- ThisCompliance friendlySystem primary support to significantly reduce back-end docking and control frictions and significantly reduce the number of institutional usersCompliance costs and access thresholdsI don't know。
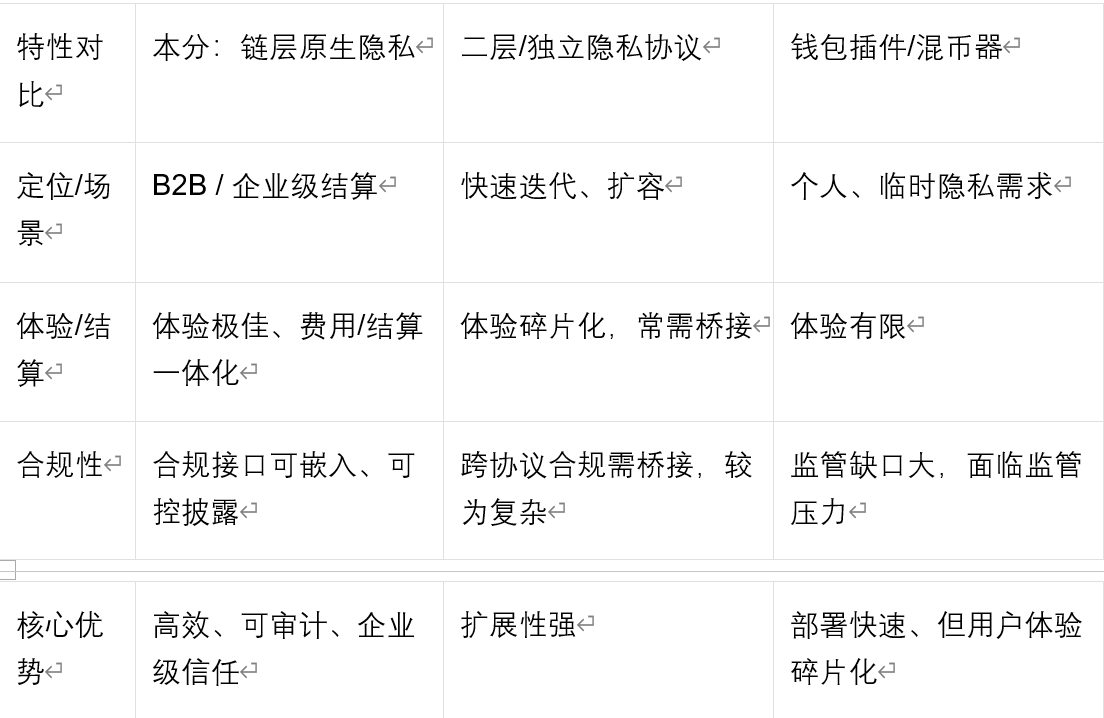
structure comparison: chain layer protozoe vs. 2nd layer vs. plugins
Stabilizing currency and privacy payments: “one side” of digital value flows and inevitable integration
THROUGHOUT THE HISTORY OF MONETARY DEVELOPMENT, EVERY LEAP IN THE PAYMENT PARADIGM, IN TX-SHIELD, IT APPEARS, STEMS FROM THE SATISFACTION OF TWO CORE CLAIMS: THE STABLE CREDIBILITY OF VALUE AND THE FREE SECURITY OF TRANSACTIONS. THIS IS THE CASE FROM THE REAL CURRENCY TO THE INSTRUMENT AND THEN TO THE ELECTRONIC PAYMENT. TODAY, WE STAND AT THE THRESHOLD OF THE NEXT GENERATION OF PAYMENTS REVOLUTION, AND THE DEEP INTEGRATION OF STABLE CURRENCY WITH PRIVATE PAYMENTS IS THE KEY TO OPENING THIS DOOR. THIS IS NOT A SIMPLE ADDITION OF THE TWO TECHNOLOGIES, BUT A NECESSARY INTEGRATION OF THE TWO SIDES OF THE DIGITAL VALUE FLOW SYSTEM — THE STABILIZATION CURRENCY BECOMES THE NEW STANDARD FOR GLOBAL PAYMENTS AND SETTLEMENTS, WHILE PRIVACY PROTECTION MEETS THE RIGID REQUIREMENTS OF FREEDOM OF TRADE, WHICH COLLECTIVELY DEFINE THE SHAPE OF FUTURE PAYMENTS, AS DO THE TWO SIDES OF A COIN。
History: Why integration is the ultimate form of digital payment
The cornerstone of the digital economy is the ability of values to flow efficiently and without friction in global networks like information. However, existing solutions are structurally flawed:
- Traditional e-payments: it relies on centralized intermediaries, expensive cross-border payments, and user data are monopolized by platforms, and privacy is impossible。
- Stable currency on the transparency block chain: As a representative of the value of the French currency on the chain, the Stable currency solves the most fundamental value scale and clearing media in the digital economy. It makes chain payments efficient, low-cost and globally available. The proportion of stable currency transactions that already account for total chain transactions is very significant and continues to grow, especially in the context of business settlements and cross-border payments. However, stability of value does not bring aboutFullness of trustI don't know. YesIt's completely public and traceableIn the chain-based environment, every transaction is a breach of commercial confidentiality. Professional analysis tools can be usedVery short course of dealingIt's even a few key transactions that clearly identify the corporate walletBusiness model, operating cost, and even strategic procurement and liquidationThis poses a significant competitive risk to enterprises。
- Private currency: It solves privacy problems, but is unable to perform payment measures and media functions because of high price volatility and lack of extensive anchoring。
History will therefore choose a necessary path: to integrate itself as a stable currency for the best payment vehicle, with the privacy guaranteed as freedom of trade. This is where the payment tool goesGrow upThe way of the inevitable。
1+1> 2: how integration can generate new paradigms that cannot be achieved by a single technology
When stable currencies and privacy payments are ingrained at the bottom of the chain, they produce much more synergy than functional overlaps。
Transition from “compliance costs” to “compliance advantages”
TX-SHIELD argues that for financial institutions, traditional privacy programmes often run counter to compliance requirements, resulting in difficult choices between “transparent exposure” and “violating privacy”. BenFen Chain integrates privacy payments and stabilization coins in the chain layer and incorporates “controllable privacy” mechanisms. This means that an enterprise can use a stable currency to make payments that are fully compliant, while implicitly protecting the details of the transaction and providing proof only when regulatory requirements (e.g. audit, judicial investigation) are in place through selective disclosure mechanisms. This has transformed privacy from a “compliance risk” to a “compliance and commercial competitive advantage”。
From "limited scenes" to "unlimited possibility" ecological eruptions
The combination of the two has unlocked business scenes previously unattainable due to privacy or payment barriers:
• Remodelling of global pay and supply chain finance:
Multinational enterprises can use stable currencies to pay their global workforce in real time, protecting personal privacy and achieving individualized financial treatment through programmability. In the supply chain, core firms can build an “auditable private clearing network” with stable currency flows between upstream and downstream firms encrypted to the public, but the overall compliance of the network can be demonstrated by regulators as a whole, significantly increasing the efficiency and control of financial flows。
• “Institutional” upgrade of DeFi:
The traditional DeFi has become institutionally ill because of transparency in trading strategies. On this sub-chain, DeFi, at the institutional level, can be born “prior to privacy” — for example, loans based on confidential transactions, DEX to prevent snipers from being robbed. The agency ' s significant financial resources, which allow it to enter safely while protecting the privacy of its strategy, will bring an unprecedented depth and mobility to DeFi。
• The next generation of consumer applications and data sovereign economies:
Users can pay subscriptions in stable currency and buy digital goods, while their consumer behavioral mapping, identity information and holding assets will be effectively protected to truly achieve “payment is service without data marks”. This provides the basis for a Web3 business model based on genuine data sovereignty。
Stabilizing currency and privacy payments are two core engines driving the chain economy towards maturity and scale. BenFen ChainThe unique positioning of the two engines is bringing together in depth to create a public chain infrastructure specifically designed for high-frequency, high-value payment scenariosI don't know. Choose the chain. Choose oneCompliance, security and efficiencyThe stable currency pays ecologically and goes directly to the next stage of the digital payment。
Sub-chain_: “highway” for privacy payments
Building a network of block chains capable of carrying large-scale commercial-class privacy payments must overcome privacy calculations at the bottom of the structurePerformance losses and economic frictionI DON'T KNOW. THE WHOLE-HOUSE SYSTEM DEVELOPED IN CONJUNCTION WITH TX-SHIELD, FROM PROGRAMMING LANGUAGE, CONSENSUS MECHANISMS TO ECONOMIC MODELS, WAS CREATED TO SYSTEMATICALLY REMOVE THESE BARRIERS AND BUILD UP INSTITUTIONAL-LEVEL PRIVACY PAYMENTSSafe, efficient and operationalThe triple cornerstone。
3.1 Move Language: "Mathematical-level trust" for the security of privacy assets
The core of privacy payments is protectionChained assetsSecurity and correct operational logic. It's designed for digital assetsMove Programming LanguageAt the root of this, it provides much more security for privacy than for privacy payments。
•Internal security:Move StrictType SystemAnd uniqueResources management mechanismsIt's over when it's doneReturn to attack, depletion of resourcesI'm not sure what I'm talking about. This ensures that core contracts involving the movement of private assets are logical and that the status of assets is clear。
•Security of reliability:Move through its ownMove Specialization Language, define pre-, post- and fixed conditions for smart contracts, and describe from the source “how the program should run correctly”. At the compilation stage, these norms will be converted toExpression in Boogie Language, and the logical validation is performed by an automated theorem. This process allows contracts to be mathematically validated for security and correctness before they go up the chain and minimizes the risk of error and loophole while running, thereby achievingVerifiable, predictable, trustedIt's a chain of implementation environments。

3.2 High performance consensus: Overcoming the ability of privacy to calculate “performance taxes”
Privacy calculations are naturally accompanied by costing and delays and must be supported by top-level performance if they are to be applied to daily high frequency commercial scenarios. It's an innovationDAG-BASED MIXED CONSENSUS MECHANISMThis challenge has been successfully addressed。
•Subsecond delay with tens of thousands of transactions per second:By distinguishing types of transactions, using “fast-track” treatment for transactions that do not involve a shared object, the chain has been achievedTransaction processing time below 0.5 secondsandTENS OF THOUSANDS OF TRANSACTIONS (TPS) PER SECOND CONTINUE TO BE IN HIGH VOLUME. IT'S A PERFORMANCE THAT MAKES COMPUTATIONAL INTENSIVEIt also allows for an “immediate completion” experience that fully meets the real-time requirements of commercial settlements。
•I'm sorryThe consensus mechanism has a high tolerance for errors (the network is stable even if partial validation nodes fail). This7x24 hours uninterruptedHigh availability is key to the reliability of privacy payment services compared to traditional financial infrastructure。
3.3 Currency of stability as “first citizen”: elimination of economic friction
One of the most revolutionary designs of the chain is to raise the stable currency to the level of the public chain“First citizen”Status. This is to remove user barriers and achieve mass adoptionThe economic cornerstoneI don't know。
•Primary integration, payment is privacy:The privacy payments directly affect the original stability of the chainNo complex cross-chain bridge or sealed assetsI don't know. It's on the chain floorAtom-grade combination of payment and privacy protectionThe middle link in introducing additional security risks and friction costs has been completely eliminated。
•Web2 flow:Users can directPayment of transaction fees in stable currency, without the need to pre-empt and hold the original currency as Gas. This design minimizes the threshold for privacy payments, with user experience like using Web2 toolsJust as naturalIt is key to promoting large-scale commercial adoption。
3.4 Modularization and interoperability: ecological flexibility for future privacy
BenFen Chain relies on the Movie languageModular designandAdvanced abstract capabilityThis provides great flexibility and re-useability to the development of top-level applications for privacy payments。
•Security module reuse:Developers can re-utilise as they build blocksSecurity module for formalisation, quickly construct complex privacy payment logic。
•Universality and Future Compatibility:Although the sub-chain is centred on the stabilization currency, its bottom structure and Move module are availableUniversal ability to pay for privacyCompatible with any assets. This flexibility ensures that infrastructure not only meets current demand for stable currency payments, but is more responsive to the evolving business landscape and innovation needs of the future。
It's not a public chain with a privacy function after the fact, it's a public chainDepth customized infrastructure to pay for privacyI don't know. It's full-scale technology selection - fromSafe MoveI don't knowHIGH PERFORMANCE DAG CONSENSUSHereStable currency integration to eliminate friction— Together constitute a top-level infrastructure that provides full support for the next generation of privacy payments in terms of safety, performance, availability and user experience。
How the chain achieves privacy payments
THE PRIVACY PAYMENT FUNCTION OF THE CHAIN, IN COOPERATION WITH TX-SHIELD, IS DESIGNED TO PROVIDE A FLUID USER EXPERIENCE WHILE ENSURING CONFIDENTIALITY OF KEY INFORMATION. WE HAVE A COMPLETE CLOSED LOOP IN DESIGN FROMPrivacy creation of assetsHereTransfer of security valueAgainControlled View and RedemptionI DON'T KNOW. THROUGH TECHNICAL INTEGRATION WITH TX-SHIELD, PRIVACY PROTECTION BECOMES THE BOTTOM FEATURE OF THE PAYMENT SYSTEM, NOT THE ADDITIONAL FUNCTION。
Creation of private assets: a step-by-step privacy starting with full value
The sub-chain has been restructured to pre-empt privacy choices。The user can decide whether to charge the token as a private form when fillingIt doesn't have to be multistep, it's more fluid。
Specific processes:
1.Initiate privacy filling or privacy token conversion:
When a user selects a filling token in a wallet, you can tick the " Filling up as a private token " option. In addition, a user may initiate an “assets encryption” transaction by means of a wallet, specifying the tokens and quantities that it wishes to convert to private forms。
2.Asset Lock:
After a transaction is confirmed by the network, a special smart contract automatically locks in a user-converted token to support the value of a private asset to be created。
3.Value Segment:
The network authentication node receives the value and uses its internal shared key and encryption algorithm to convert it into a unique, irregular set of data fractions。
I'm sorry.Document Generation:
The system creates a new “private asset” object for the user and stores this newly generated data set。
5.Completed:
When the transaction goes up, the user's public token is locked, and an equivalent private asset, in the form of encrypted fractions, is acquired, the true value of which is no longer visible in the chain。
This “fill-or-privilege” mechanism removes user thresholds for access to privacy assets and makes privacy protection a default option for chain operations rather than a complex additional process。
Privacy payments
When a user holds a private asset, payment can be made without disclosing the details of the transaction。
& nbsp; below displays the core process of privacy payments using user A to user B as an example:
1.Deal Build:
A'S WALLET CREATES A TRANSACTION, IDENTIFIES THE RECIPIENT AS B AND SETS A SPECIFIC AMOUNT OF PAYMENT. IT THEN INITIATES A REQUEST FOR AUTHORIZATION FROM A CREDIBLE CERTIFICATION NODE, REQUESTING THAT THE AMOUNTS PAID BE PROCESSED INTO TEMPORARY ENCRYPTED FRACTIONS。
2.Submit Network:
THE WALLET WRAPS UP THE INFORMATION REQUIRED FOR THE EXECUTION OF THE EXCHANGE AND SUBMITS IT TO THE NETWORK. THE TRANSACTION CONTENT WILL INCLUDE THE CURRENT BALANCE FRACTION OF A, THE CURRENT BALANCE FRACTION OF B, AND THE ENCRYPTED FRACTION OF THE PREVIOUS STEP THAT REPRESENTS THE TRANSACTION AMOUNT。
3.Backstage Operations:
The network authentication node receives the transaction, uses the shared key to decrypt and calculate the three fractions, and then re-encryptizes the result into a new encrypted fraction。
I'm sorry.Status Update:
THE CALCULATION WOULD RESULT IN TWO COMPLETELY NEW DATA FRACTIONS - ONE REPRESENTING THE REDUCED BALANCE OF A AND THE OTHER REPRESENTING THE NEW BALANCE OF B. SUBSEQUENTLY, THE SYSTEM UPDATED THE TWO NEW SETS TO PRIVATE ASSET OBJECTS A AND B, RESPECTIVELY。
5.Transactions completed:
THE TRANSFER OF VALUE IS COMPLETED WHEN THE TRANSACTION IS CHAINED. FOR ANY OTHER CHAIN USERS, THEY CAN ONLY SEE CHANGES IN DATA FROM THE PRIVATE ASSET OBJECTS OF A AND B, BUT THE SPECIFIC TRANSACTION AMOUNTS ARE NOT KNOWN。
View and redeem privacy assets
1.Request initiated and signed:
Users initiate requests through wallets to a credible network node. The request is accompanied by a digital signature generated by the private key of the user ' s wallet to prove the identity of the owner。
2.Organisation:
Upon receipt of the request, the legality of the signature is verified, confirming that the claimant is the legitimate owner of the chain of records of the private asset. Authentication is primarily used to prevent unauthorized access by other users。
3.Lower chain:
After validation, the trusted node will read the user's encrypted fractions from the chain and, in its local memory, return them to the user-readable real balance values using a shared key。
I'm sorry.Safe return or redemption:
oView: The real balance will be displayed at the front end of the wallet sent back to the user through a secure encryption channel。
oRedemption: The user may authorize the transaction to destroy the privacy asset certificate in its possession on the chain. Once the destruction is confirmed by the network, the equivalent public token initially locked will be automatically released and returned to the user。
The privacy payment system in this chain is passedFull value is privacy, partial encryption flow, controlled and transparent foreclosureIn three phases, a complete, verifiable and regulated privacy payment closed loop was constructed. This system is not an additional function of an external plugin or layer of protocol, but rather a primary capability at the bottom of the public chain. It makes privacy protection the default option, gives natural confidentiality to stable currency settlements, and allows businesses and individuals to achieve genuine private payments subject to compliance。In this chain, privacy is no longer “additional protection”, but part of the payment itself。
Core technology for the payment of privacy in the chain
SECURE TRANSACTION ARCHITECTURE BASED ON FAST MPC AND REGULATORY ENGAGEMENT
In conjunction with TX-SHIELD, this sub-chain of privacy payments combines systemic innovations to integrate block chain technology (Block Node), rapid multi-counting (FAST MPC) and regulatory compliance mechanisms (Regulator) to achieve “accessible data” for asset transfers in distributed networks。

I. Core system objectives
THE MAIN OBJECTIVE OF THE SYSTEM IS TO ADDRESS TWO CORE CONTRADICTIONS IN TRADITIONAL BLOCK CHAIN TRANSACTIONS: PRIVACY PROTECTION AND REGULATORY COMPLIANCE, AND PRIVACY PROTECTION, WHICH MEANS THAT THE SYSTEM CAN ENSURE THAT SENSITIVE INFORMATION SUCH AS TRANSACTION AMOUNTS, PARTICIPANTS ' IDENTITIES, ETC., ARE NOT PUBLICLY EXPOSED TO THE CHAIN IN AN EXPLICIT FORM IN ORDER TO ACHIEVE CONFIDENTIALITY OF TRANSACTION CONTENT WHEN USER A TRANSFERS ASSETS TO B. REGULATORY COMPLIANCE MEANS THAT WHILE PROTECTING PRIVACY, THE SYSTEM CAN SET ASIDE THE NECESSARY MECHANISMS TO ALLOW AUTHORIZED REGULATORS TO DISCLOSE AND AUDIT TRANSACTION DETAILS SAFELY AND IN A CONTROLLED MANNER, SUBJECT TO SPECIFIC NEEDS. DETAILS OF HOW THIS FUNCTION IS ACHIEVED THROUGH FAST MPC WILL BE PRESENTED LATER. IN ADDITION, IN THE CURRENTLY PUBLISHED VERSION, ALL PAYMENTS FOR THE PRIVACY OF THE CHAIN ARE REALIZED USING MPC, BUT A NEW, MORE COMPLEX BUT MORE POWERFUL VERSION OF THE MPC-FHE COMBINATION WILL GRADUALLY BE INTRODUCED IN SUBSEQUENT VERSIONS:
II. Key technical components
There are several major core components in the system: Block Node, Fast Multi-Cluster (FAST MPC), Key_shard. A presentation will be made below:
1. block node (Block Node)
Block nodes, which are at the heart of the distributed ledger system, are responsible for the validation, consensus and storage of transactions. All transactions (whether Plain TX or Commercial TX) need to be processed through these nodes。
2. Quick Multi-Calculation (FAST MPC)
FAST MPC is the core technology for the system to achieve privacy protection. MPC allows participants to calculate a predetermined function together without disclosing their input data. The “FAST” highlighted the targeting and efficiency of the MPC programme, which was optimized to meet the requirement of high throughput of block chains. The MPC module operates internally in Block Node, with the main functions of processing Key_Shard and User Private Meta Data to generate or validate confidential transactions. In the original version of this sub-chain, the functions of the FAST MPC are relatively limited, but through STL research, a higher version of the MPC can be found that can be integrated with other password protocols such as HE, adding more functionality to be involved in transactions and to increase the privacy and security of transactions in regulatory settings. And provide a faster and faster batch operating version。
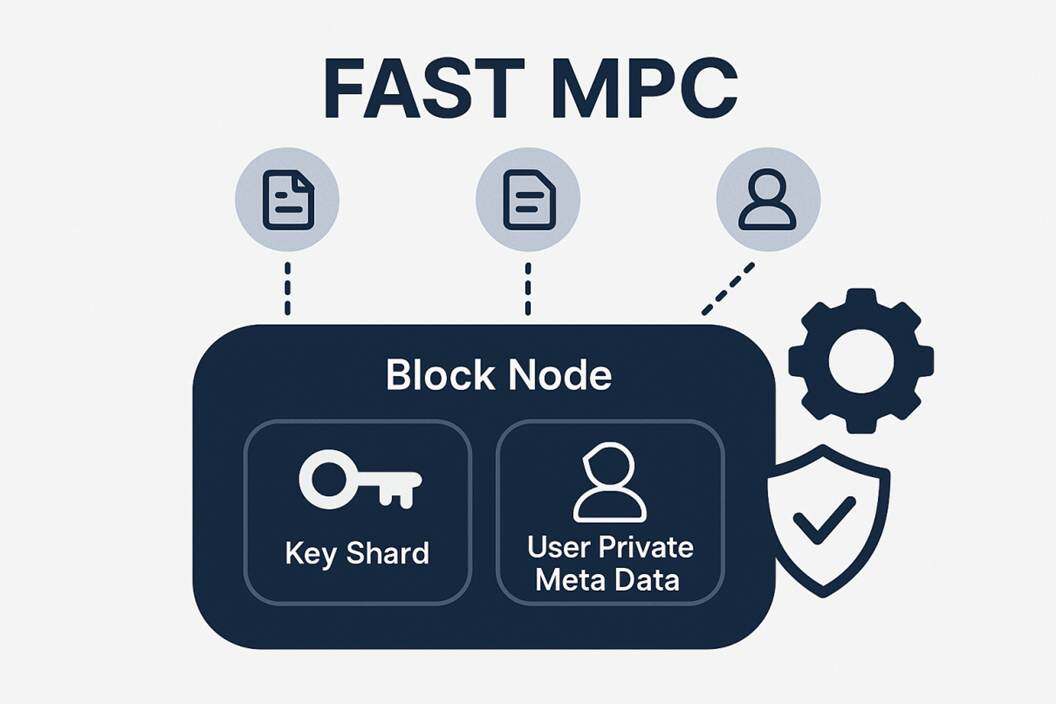
3. Key_board)
THIS IS A KEY ELEMENT FOR ACHIEVING DATA SECURITY AND REGULATORY INTERVENTION, PRODUCED BY THE FAST MPC MODULE。
Users ' private metadata are encrypted or split into multiple key fractions, held by different entities, such as Block Node and Regulator. And you can access or decrypt the core of User Private Meta Data only if you bring together Key_shard from different sources (e.g. Block Node and Regulator)。
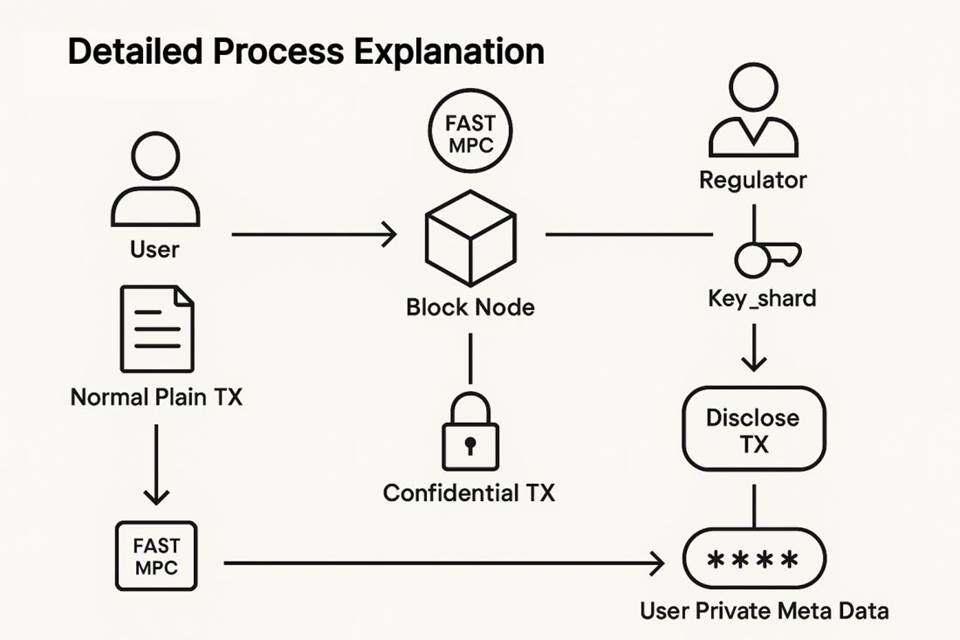
III. Process details
1. Initiation of ordinary transactions: The user initiates the transfer of assets by a Normal Plain TX (common express transaction)。
2. Generating confidential transactions: transactions entering Block Node. The system's FAST MPC module uses the key fraction it holds to process User Private Meta Data to generate an encrypted Commercial TX. This confidential transaction was sent back to Block Node for chain processing。
3. Regulatory intervention points: Regulator (supervisor) is a special participant in the system and holds Key_shard。
4. Disclosure of transactions: When supervision or audit of a particular transaction is required, Regulator initiates the Disclos TX request. The request, combined with Key_shard held by Regulator, went to User Private Meta Data. This means:
a. Regulator's key fraction is combined with the Block Node's fraction for restoration or access to User Private Meta Data。
b. Conditional and controllable disclosure of the contents of the Control TX may only be made through the MPC or declassified mechanism after the regulatory process has been triggered and the authority of the Regulator has been validated。
The bright spots and differential advantages of payment for privacy in the chain
Privacy and user experience are often difficult to combine on the road to mainstream application of block chains。This sub-chain increases privacy payments from an “optional function” to a chain-level primitive capacity, with several agreements and product-level innovations that significantly lower the threshold for use and meet institutional compliance needs. The following are the core highlights and differential advantages of this share of privacy payments。
Full-dimensional privacy protection
Privacy protection is no longer limited to the amount of the asset, but extends to all sensitive dimensions of the transaction and provides different levels of protection through the source of passwords。
- All transaction data hidden
TECHNICAL CORE: DEPTH INTEGRATION MPC AGREEMENT AND ZERO KNOWLEDGE CERTIFICATION. THE ORIGINATOR OF THE TRANSACTION CO-GENERATED THE TRANSACTION WITH THE PARTICIPANTS THROUGH THE MPC AGREEMENT UNDER THE CHAIN. IN THIS PROCESS, ALL KEY FIELDS OF THE TRANSACTION, SUCH AS THE INPUT AMOUNT, THE OUTPUT AMOUNT, THE SENDER ' S ADDRESS, THE RECIPIENT ' S ADDRESS AND THE TYPE OF ASSET, ARE CONVERTED INTO A STATE OF ENCRYPTION OR COMMITMENT, AND ONLY THE FINAL VALID STATUS CHANGE IS SYNCHRONIZED WITH THE BLOCK CHAIN. THE NETWORK NODES ONLY VERIFY THE CORRECTNESS OF THE STATE CONVERSION, AND CANNOT EXTRAPOLATE ANY ORIGINAL TRANSACTION INFORMATION, CUTTING THE POSSIBILITY OF CHAIN DATA ANALYSIS FUNDAMENTALLY。
- Bulk privacy transactions and group settlements
- TECHNICAL CORE: MPC BATCH PROCESSING BASED ON AUTHENTICATION OF ENCRYPTION AND AGGREGATE SIGNATURES. GIVES A BATCH-VERIFIABLE ANONYMOUS IDENTIFIER TO A BATCH OF TRANSACTIONS BY EMBEDDING A VERIFIABLE RANDOM FUNCTION IN THE MPC PROTOCOL. THIS ALLOWS THE CERTIFIER TO PERFORM A ONE-TIME VALIDATION OF THE LEGITIMACY OF THE ENTIRE BATCH, RATHER THAN A CASE-BY-CASE PROCESS。
- Private transfers of assets
Technical core: Key encryption and access control. Each encrypted transaction record is linked to one or more symmetric/asymmetric keys. Only participants with the corresponding decryption key can decrypt and see the transaction details. This resulted in a return of ownership of the data and ensured that transaction records became private journals, not public accounts, open only to interested parties。
- Provisional Visible Authorization
Technical core: Attribute-based encryption or proxy heavy encryption. The key owner does not need to disclose all confidential data when it is necessary to provide information on transactions to the auditor, regulator or judiciary. They can authorize third parties to decrypt a specified transaction record within a given time period by generating a time-limited, specific range access token or by performing a proxy re-encryption. Access rights automatically expire after the expiry of the authorization。
Internal and programmable Regulatory
Regulatoryity is not an external function to be added ex post facto, but is designed as a core feature at the level of the agreement, balancing “privacy protection” with “compliance regulation”。
- Selective disclosure
Technical core: zero knowledge certification and layered key system. Different properties of the transaction are encrypted and controlled by different keys or zero knowledge proof systems. Users may selectively disclose specific information without having to disclose all data, depending on regulatory or business needs. For example, tax authorities can be shown that the amount of the transaction meets a certain threshold without disclosing the counterparty。
- Authority for enterprise-level audit nodes
- Technical core: door-limited signature and dynamic authority management. An enterprise can anticipate an audit strategy to distribute access keys to selected transaction data to designated audit nodes through smart contracts or chain agreements in a limited manner. Only when preset conditions are met can key re-engineering and data access be made, both to ensure the need for intra-firm governance and to prevent mono-point abuse。
- Protocol layer embedded compliance interface
TECHNICAL CORE: MODULARIZED PASSWORD PACKAGES AND STANDARDIZED REGULATORY API. PASSWORD COMPONENTS SUCH AS MPC, FHE, ZKP ARE NOT CALLED IN THE FORM OF ATTACHED API, BUT ARE AN INTEGRAL PART OF CONSENSUS MECHANISMS AND STATE CONVERSION FUNCTIONS. REGULATORY RULES CAN ENSURE THAT COMPLIANCE CHECKS ARE CARRIED OUT AUTOMATICALLY WITHOUT DISCLOSING PRIVACY BY VALIDATING THE PERFORMANCE OF OFFLINE CONTRACTS AT THE OFFLINE PHASE OF THE MPC OR ON THE CHAIN。
- Declassification thresholds based on legal procedures
Technical core: distributed key generation and door decryption. The system foresees a regulatory public key that is controlled by multiple parties. The corresponding private key is held in a limited section. Only when a legitimate judicial order is obtained can these independent parties work together to enforce a door-limit decryption agreement, restore the primary key and decrypt the trade history of a given address. This process is transparent, auditable and multi-stakeholder, preventing unilateral controls。
High performance architecture and achievement
Barriers to traditional privacy technology have been addressed through password innovation and system architecture optimization。
- IMPROVED MPC INTEGRATION STRUCTURE WITH ADVANCED PASSWORDS (PROJECTED)
TECHNICAL NUCLEUS: FHE-MPC HYBRID MODEL AND PORTFOLIO CERTIFICATION. WE PLAN TO ADOPT A HIERARCHICAL CODE STRUCTURE. AT THE BOTTOM, THE DATA ARE CALCULATED IN A CONFIDENTIAL MANNER USING AN EQUIVALENT ENCRYPTION TO ENSURE THAT THE DATA ARE NEVER DECRYPTED DURING THE CALCULATION. AT THE UPPER LEVEL, THE MPC PROTOCOL COORDINATES FHE CALCULATIONS AND HANDLES COMPLEX LOGICAL JUDGEMENTS. IN ADDITION, THE USE OF ZERO-RELEASE KNOWLEDGE TO PROVE THAT MULTIPLE TRANSACTIONS OR STATE UPDATES ARE COMBINED INTO A SINGLE, SMALL VOLUME CERTIFICATE HAS SIGNIFICANTLY REDUCED THE COST OF CHAIN DATA STORAGE AND VALIDATION AND HAS ACHIEVED “FULLLY ENCRYPTED FRACTIONS AND RESTORATION”。
- Second-degree privacy confirmation time
○Technology core: All online processing is currently used, and two phases of offline/online calculation and flow line optimization are expected in the future. Most computing-intensive operations are pre-completed in the offline phase. The online phase requires only lightweight authentication, signature and consensus agreements. This design decorates the chain ' s recognition of time and complexity of transactions, which can reach a second stage regardless of the complexity of the backstage logic. Our baseline tests show that on standard commercial hardware, the system conservatively estimates that 1,000+ privacy transactions/secs can be processed and that, as algorithms optimize and hardware accelerate, performance will have the potential to upgrade at a numerical level to fully meet the needs of future high-frequency financial operations。
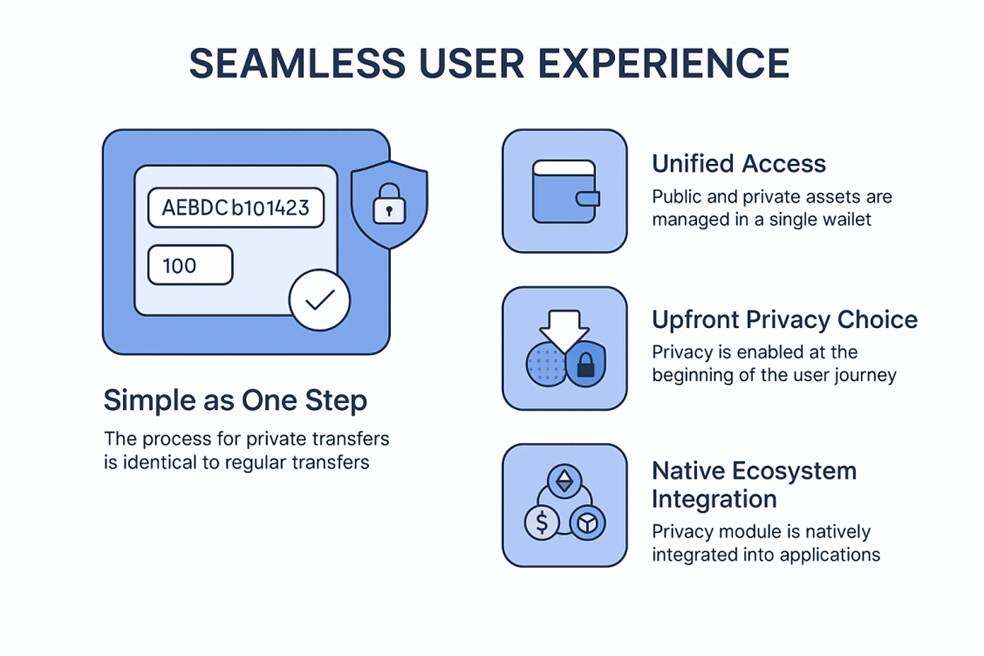
Extreme user experience
The privacy function of the traditional block chain is usually “outside” and requires additional user learning processes. This sub-chain is dedicated to making privacy protection the unsure default experience of users。
The operation is simple: the steps taken by the user to make a private transfer are identical to the normal transfer. Enter the address and amount in the wallet and confirm that privacy protection is automatically completed in the backstage, eliminating additional learning costs. This design concept is in line with the exploration of industry to enhance the availability of block chains。
Unified access management: Users do not need to install multiple wallets or plugins to manage open and private assets seamlessly under the same wallet address and can view the corresponding balances at any time. This harmonization has greatly simplified the asset management of users。
Pre-privileged privacy choices: the pre-filling of privacy choices through designs such as "fill or privacy" makes privacy protection the starting point for a user's journey, rather than an additional option for ex post remedies。
Eco-protocol synergies: Upper-level applications such as BenPay Ecology, RWA release, and DeFi protocols allow for primary calls to privacy modules and experience seamless access. HereBen Pay DeFi EarthandBen Pay CardFor example, when a user is involved in a currency-making strategy, the process of filling, changing shares and foreclosure is encrypted through BenFen's original privacy module. The protocol could validate the operation, but the user position, the size of the proceeds, or the act of repositioning could not be seen outside, making BenPay DeFi a secure DeFi entry point. _Other Organiser In the case of online payments or offline consumption, the encryption of money, payment paths and account information is not visible to the business as well, and observers are unable to construct consumer images, thus achieving privacy stabilization currency cards and real-life Web3 consumption experiences. The entire ecology has a consistent and seamless privacy experience in payment, trading, consumption and asset allocation, based on the original Layer1 privacy design。
Zero Gas Fee Experience
Gas fees are one of the main thresholds preventing ordinary users from entering the Web3 world, especially from using high-complex privacy functions. The sub-chain has been innovative through a layer of agreements, reshaping the structure of transaction costs。
Sponsoring transactions: This sub-chain separates the role of the “founder” of the transaction from that of the “Gas payer” at the level of the agreement. This allows project or commercial parties to pay Gas fees directly for users, which are simple, safe and efficient. For users, this means that when payments are made using privacy, there is no need for care and payment of Gas fees。
Stabilized currency payments to Gas: Users can also pay the Gas fee directly using the system ' s original stable currency, without having to hold additional tokens to simplify asset allocation。
Natural stabilization currency structure
Unlike stabilization currency, which relies on smart contracts, the chain constructs multi-currency stabilization currency as a “first-class citizen” of the chain, which provides a more solid base for privacy payments。
Chain layer, security tops: Stable currency, as a primary asset at the bottom of the public chain, does not depend on the logic of smart contracts, fundamentally circumventing the risk of contractual loopholes and is more secure。
Eco-extensibility
The value of a technology depends on its ecological prosperity. It lowers the threshold of access for developers and businesses through open design。
STANDARDIZED INTEGRATION: THE PROVISION OF FULLY FUNCTIONAL AND WELL-DOCUMENTED SDK INTERFACES WITH API TO FACILITATE THIRD-PARTY WALLETS, COMMERCIAL HOUSEHOLD SYSTEMS AND FAST-INTEGRATED CROSS-CHAIN BRIDGE PRIVACY PAYMENTS SIGNIFICANTLY REDUCES DEVELOPMENT COSTS。
Support for de-centreized commerce: Both the centralized electric powerer platform and the de-centreded DApp provide users with a wider range of payment options through the rapid deployment of the private collection module with the tools provided by the chain. BenPay ' s access has also validated the viability of this capability in a real payment scenario, providing templates for more future commercial applications to land。
Bulk privacy payments
The bulk privacy payment function of the chain is a perfect combination of efficiency and privacy for high-frequency, multi-target payment needs such as corporate payroll, project airdrops and community awards。
Efficiency multipliers: Users can complete accurate distribution of privacy assets to hundreds or even thousands of addresses in one operation by group selection or uploading Excel templates, leaving out the cumbersome single operation。
Protection of privacy and compliance: All volume transactions are carried out in a private computing environment, ensuring the complete confidentiality of each amount and receiving information, protecting both the privacy of the recipient and the confidentiality of the financial information of the issuer。
Any currency payment for privacy
Prophecies support: Privacy payment mechanisms in the chain do not depend on specific asset types. Access to the privacy payment system is available as long as the asset has a system-supported clearing and recording capability. Users are free to convert tokens into private forms of transfer and receipt of a single key。
The privacy payment system of the chain, through original innovations, covers complex privacy techniques in a simple user experience; removes user thresholds through a revolutionary zero Gas fee model; lays the foundation for security and globalization through a bottom-up integration of the original stable currency; and extends its capabilities to scenarios from individuals to enterprises through open eco-efficient bulk functions. This marks the maturity of a complete set of solutions that truly combine privacy, availability and scalability, and is not only a breakthrough in technology, but also a critical step in moving sector chain privacy payments towards mainstream application。
THE PRIVACY ENFORCEMENT CAPACITY OF THE SUB-CHAIN IS BASED ON TX-SHIELD ' S SUB-CIPHERIC STRUCTURE, WHICH INTEGRATES ITSELF AT THE CHAIN LEVEL AND TOGETHER CONSTITUTES THE INFRASTRUCTURE FOR STABLE CURRENCY PRIVACY SETTLEMENT. AS THE SYSTEM EVOLVES, WE WILL CONTINUE TO DEEPEN IN THE CONTEXT OF CONFIDENTIAL ENFORCEMENT, REGULATORY STRUCTURES AND INSTITUTIONAL-LEVEL PAYMENT SCENARIOS, PROMOTING THE SCALING DOWN OF PRIVATE SETTLEMENTS IN THE FINANCIAL AND COMMERCIAL SPHERES。
AboutBenFen
BenFen is a high performance public chain specifically designed to stabilize currency payments. We have built a secure, low-cost and highly scalable bottom-up network based on the Move language. Its core feature is supporting users to pay the Gas fee directly in stable currency, which significantly reduces the threshold for use and paves the way for large-scale applications. On the basis of its strong cross-chain and multi-currency clearing capacity, the chain covers multiple payment scenarios through rich ecological applications. More importantly, we provide enterprise-level users with critical privacy payment options to ensure that they benefit from block chain efficiency advantages while protecting core business data from disclosure。
It is dedicated to becoming a global network of stable currency flows for service enterprises that pay, cross-border payments, electricians and offline traders, a next generation of financial infrastructure that combines efficiency, cost and safety。
AboutTX-SHIELD
& nbsp; TX-SHIELD is a regulated chain privacy infrastructure that provides both parties with privacy, control and visual payment and settlement capabilities for the application of the stable currency and block chain。
Core solutions:
- Tx-SHIELD:Privacy infrastructure for block chain applications to achieve confidential transactions, Dark Pools and privacy-centred protocols。
Our innovation:
WE NOT ONLY PROTECT THE PRIVACY OF TRANSACTIONS, BUT ALSO RECREATE THE TENURE AND SECURITY OF ASSETS THROUGH DISTRIBUTED PASSWORDS. THE TX-SHIELD PROGRAMME ENABLES BUSINESSES AND FINANCIAL INSTITUTIONS TO CO-HOST ASSETS, PRIVATE LIQUIDATION AND REGULATED COMPLIANCE AUDITS WITHOUT DISCLOSING BUSINESS SECRETS。
We are building an infrastructure like this:Let privacy no longer become an obstacle to regulatory and institutional adoption, but rather a shield for financial flows。
TX-SHIELD – & nbsp; The private and regular settlement base-player for stalecoin, blockchain and input.